Using PeopleForce data in user-facing solutions
Many customers choose to use PeopleForce data as part of user-facing solutions. Examples of this include:
- Looking up a list of employees
- Retrieving leave requests
- Retrieving directory information such as Positions or Departments
- Showing a list of vacancies on a website
When building such a solution, it is essential that developers implement this correctly to avoid creating security risks through exposing employee data.
In the case of showing vacancies on a website, we have a dedicated Career API Key that can be used for this. See the guide for own career site integration.
In all other cases, it is essential that developers create a solution that does not expose the API Key in the web browser (frontend) and instead protects the API Key in a proxy service. This is important for public and internal solutions - even if a solution is not public, an API Key exposed to your team presents a data security risk.
One such way to protect against this is to implement a "2-tier architecture" as shown below:
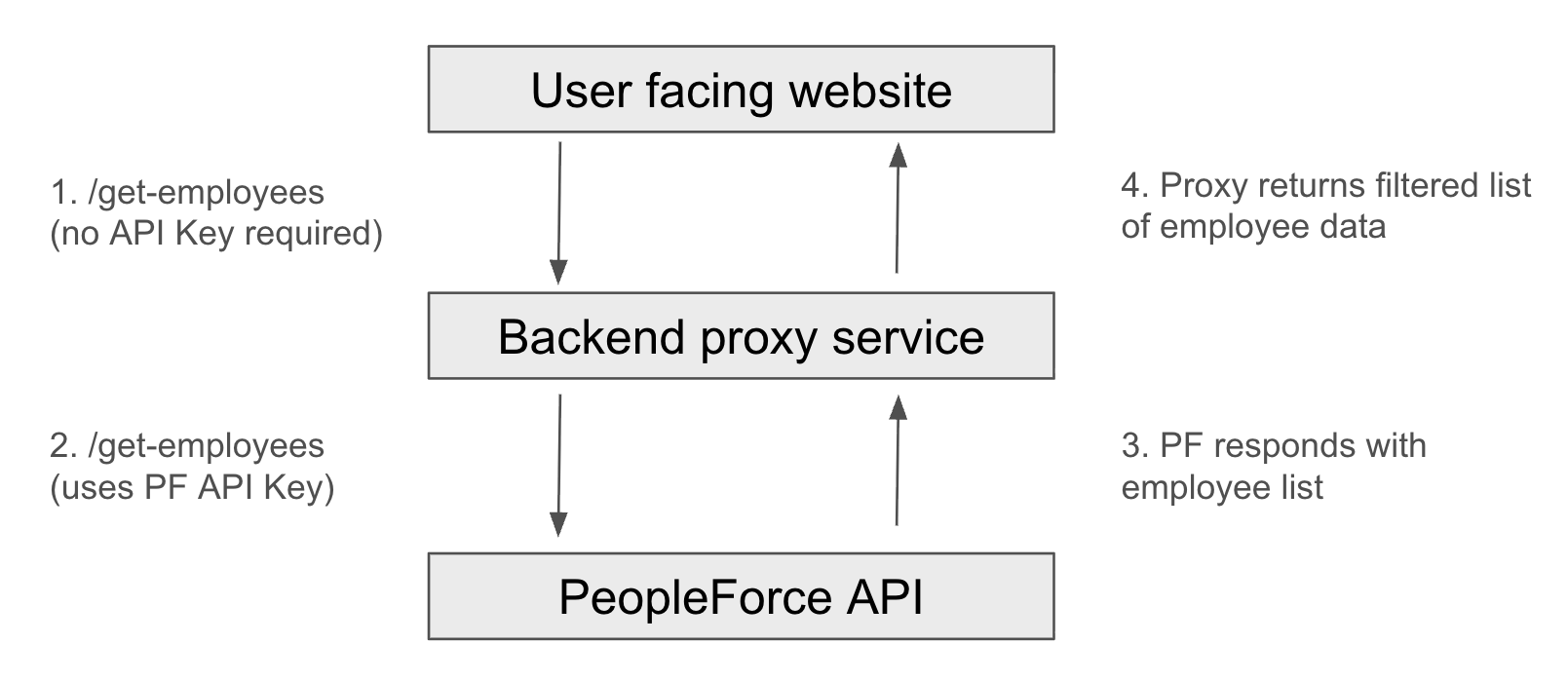
In this example, the user facing website needs a list of employees.
Step 1: The website will request a list of employees from your backend proxy service. This request doesn't reference any API Key from PeopleForce.
Step 2: The backend proxy service receives this request, and in turn will call PeopleForce to retrieve a list of employees, potentially filtered based on the use case. It will also know the PeopleForce API Key and use this in the background to retrieve the employee list
Step 3: PeopleForce responds to the backend proxy service request with a list of employees.
Step 4: The backend proxy service may filter or reduce the data returned from PeopleForce to ensure only essential data needed by the user facing website it returned.
This solution protects the PeopleForce API Key by encapsulating it in the backend proxy service.
Updated 3 months ago
